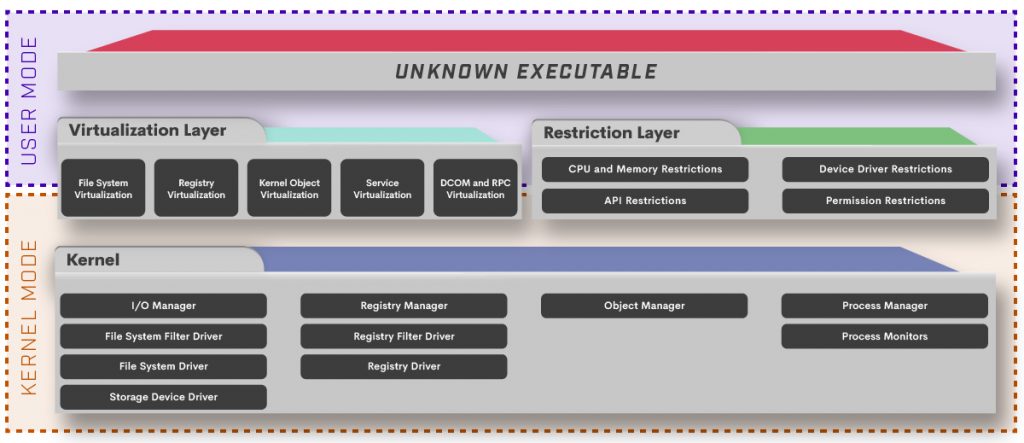
Comodo’s patented “Kernel API Virtualization” – Under the Hood
When it comes to securing your enterprise endpoints, it’s important to have a foundational understanding that there are three types of files: the good, the bad and the unknown. Approaches such as Antivirus (both vendor-branded “next gen” and legacy detection-based), Blacklisting and Whitelisting handle the known good and the bad files – but what about…
Read more
Recent Comments