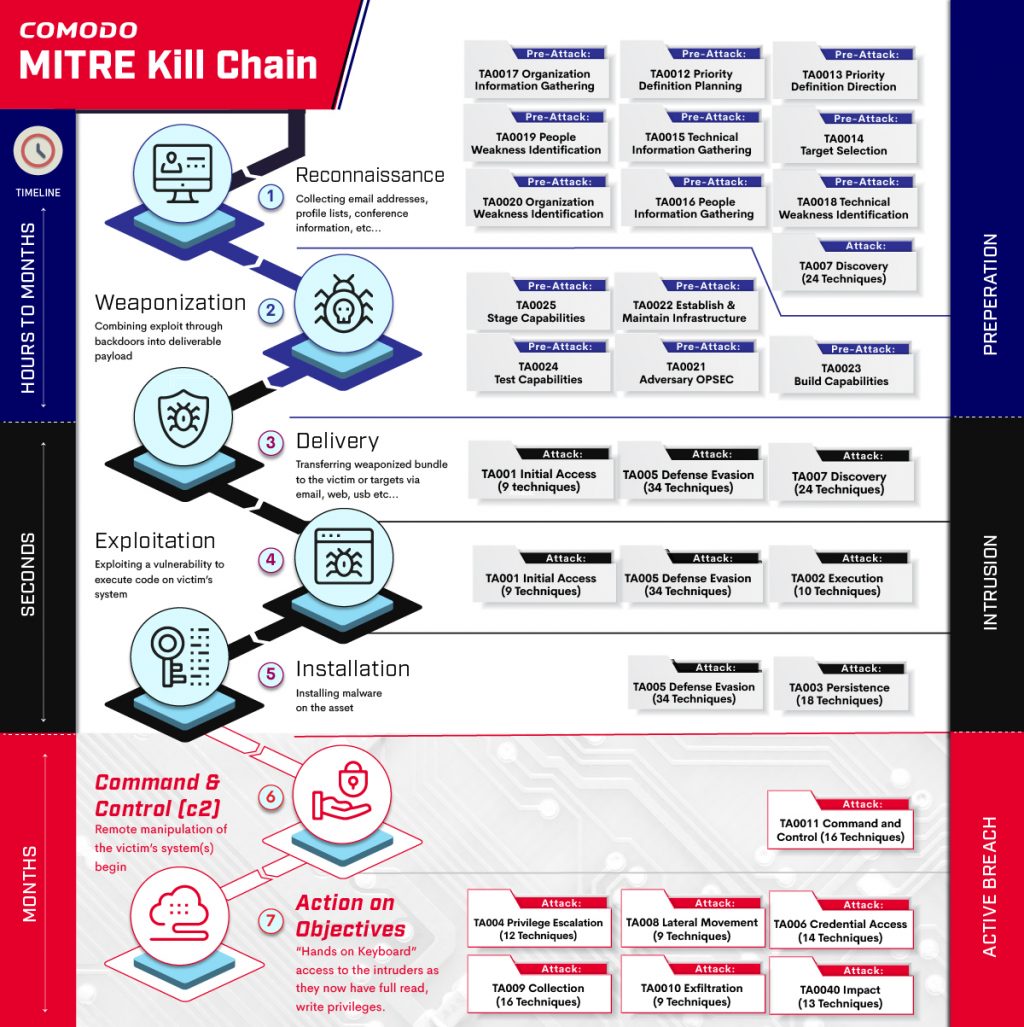
Comodo MITRE Kill Chain
Cyber Intrusion Kill Chain aka Kill Chain, has been adapted from military concepts. Locked Martin’s engineers was the first to adapt it to cyber security area. The core of framework has been arisen from the structure of attack. It describes an end-to-end process , or the entire chain of events, that is required to perform…
Read more
Recent Comments