Applying Attack Surface Reduction on top of Attack Surface Reduction : ASR2
First some definitions/terminologies so that we all know what we are talking about
Threat Actor: A threat actor or malicious actor is a person, entity or an object responsible for an event or incident that impacts, or has the potential to impact, the safety or security of another entity. In Cybersecurity this can only be a “Human” or an “Executable file” (Executable file is any type of a file that sends instructions to the CPU either directly or through interpretation)
Security Posture: is overall security status of all enterprise inventory consist of software hardware assets, networks, services, people, information etc. where covers also security controls and measurements, cyber defense systems and enterprise readiness to react, response and recover from security incidents.
Attack Surface: The sum-total of points on systems (or networks) where an adversary can try breach to the information systems. It is all possible techniques and paths that an attacker can use to gain unauthorized access to company’s assets. (Attack surface of your home, from burglar’s perspective could be your doors, windows, chimney, basement, garden etc )
Attack Vector: An attack vector is a path or means by which a hacker can gain access to a computer or network server in order to deliver a payload for malicious outcome. In most cases attack vectors enable hackers to exploit system vulnerabilities.
Vulnerabilities: Official definition of vulnerability is a weakness which can be exploited by a threat actor. We can also define it as deviation of intended behavior of the system due to intended or unintended manipulation of system inputs or states.
So if we use those terms and define them all on the same context, An attack vector is a path or means by which a hacker can gain access to a computer or network server in order to deliver a payload for malicious outcome. In most cases attack vectors enable hackers to exploit system vulnerabilities. All possible attack entry points on systems are collectively termed as “attack surface”. Security Posture of the enterprises might have millions of possible attack entry points “attack surfaces”, some of them have controls or counter measures from attacks, some of them still open to be exploited. But basically systems without an attack surface is impossible.
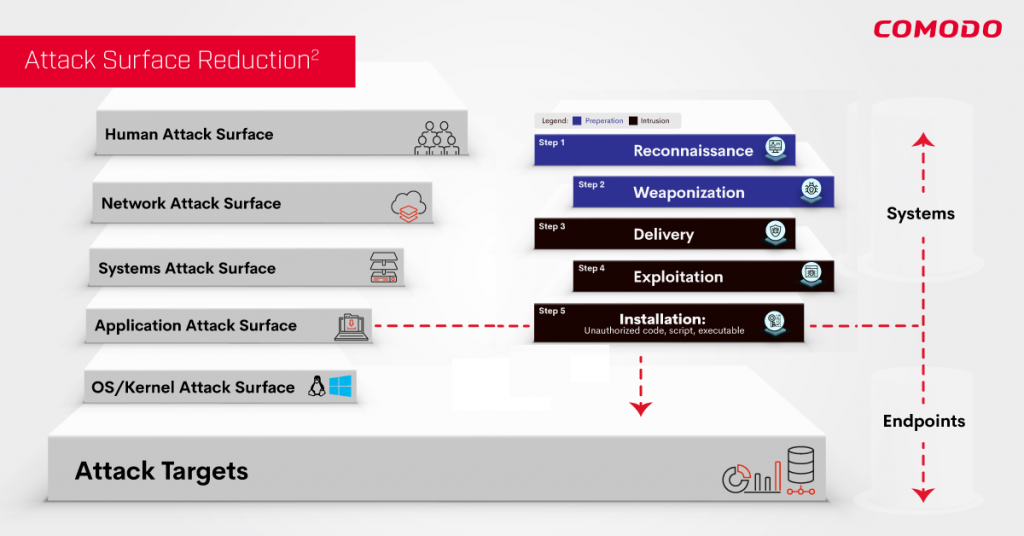
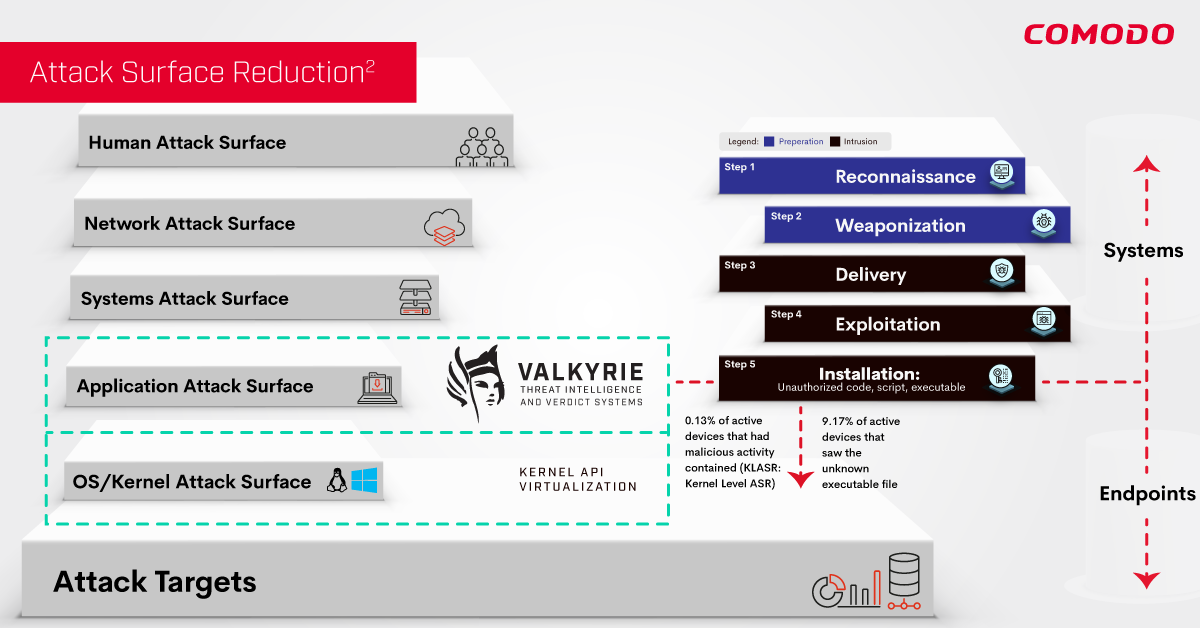
Lets look at all the categories of attack surfaces:
- Human Attack Surface
- Network Attack Surface
- Systems Attack Surface
- Application Attack Surface
- OS/Kernel Attack Surface
Human Attack Surface
Defines all type of errors, mistakes or malicious intentions by human actors internal to the organization. Regardless of how many technical controls implemented, no matter how few processes and data resources exposed to the external world. Users will always be one of the biggest sources of an attack that allow attacks with a click of the mouse or replying back to a phishing email. Security awareness training is one of the techniques that train employees on behavior necessary to maintain security policy compliance. Separation of duties, enforcement of least privilege to the users of the system and keep need-to-know principles are also necessary at this step. All these steps help apply “Attack Surface Reduction” to “Human Attack Surface”.
Network Attack Surface
Having external boundary of the systems, the network attack surface can be the biggest among all other categories. This covers all external attack paths starting from reconnaissance to delivery. The attacker can be outside to the organization or insider where he needs to penetrate into the network defenses first. At this step we can define external trust boundaries to exist between systems, network segments and organizations. Before any data transfer or critical actions take place through the boundary, defining and mandating a trust boundary is necessary. Requests for services or data from outside of a system are a required component of the action/condition chain required for malicious control of a target. On network level, this can be granted by properly segmented network. To reduce attack surfaces on network, defining level of trust and creating trust boundaries are necessary. Trust levels should start from organization to organization and extends to external business partners, customers, remote employees, and cloud services. Once trust-levels are defined, segmentation of the network while keeping the same trust-level networks communicating can be achieved. For any other connectivity. Developing enterprise network edge and a data center trust boundaries can deny malicious access to systems, processes and data resources.
System Attack Surface
A system is the combination of hardware and software components as well as users/systems with access to the system, process and with ability to change the data. Systems can be on the same network or expand to a number of networks due to dependency of external systems or data. The first step in reducing attack surface should be discovering all system components, internal and external system dependencies. This will isolate and then break down the system components into different trust levels. As in network attack surface reduction, we should also define trust boundaries. System trust boundaries exist both internally and externally where a trust boundary separates two systems or their processes. Establishing a trust relationship requires verifying the identity and applying appropriate set of access rights managing communication channel between.
External trust boundaries exist between systems, network segments and organizations. Anytime two systems connect, whether system itself or enterprise, they share a common attack surface. Attack surface of system A will depend on processes of system B, which system A depends on. This attack surface should be governed by set of access rights between A-B. In addition to that, both systems can require identity verification before establishing common sessions. The same is true of Web services or other processes that might request use of a process or data resource from another system. Organization to organization communication is also another channel of connection that needs to be investigated at this level of attack surfaces. When an organization establishes connection with another organization, its attack surface is extended to that of the external entity, with a trust boundary between them. Two actions help retain an acceptable attack surface: assurance of the external entity’s expected levels of trust and strong trust boundary management.
Attack surface at system level can be controlled and reduced by carefully selected access rights. Subject-Object model can be constructed where subjects can be a system process, other systems or user itself, objects can be system process or data inside the system. System processes or data as objects which are accessed by subjects should be controlled by access rights on the channel of communication. The Channels/Protocols represent the communication media, which could be as basic as offline messages, emails, user interfaces or synchronous API calls between two different systems. If we model this definition, as A system attack surface is the total of all exposed processes/data resources and allowed channels/protocols as constrained by the existing set of access rights. We end up with this formula.

So in order to reduce the attack surface at system level, we need to reduce the number of exposed processes, data resources and reduce number of channels, however most of the time this can not be applied easily without negatively effecting system functionality. Therefore increasing system access rights and carefully designing it so that it will govern all channels and all data resources is one of the more practical ways of reducing the attack surface.
Application Attack Surface:
At this level, we are operating at the endpoint or server level and applications running on these are creating an attack surface that requires protection. Traditional endpoint protection solutions like Host-Based Firewall, NextGen-AV, Host-based IDS etc are good examples for this level. There are also basic ASR techniques applied by operating systems like universal extensible firmware interface (UEFI), operating system module and driver verification, Kernel and Memory integrity protection: Kernel Data Protection (KDP), Address Space Layout Randomization etc. for this level.
Here are some basic examples of attack surface reduction techniques for this level
- Hardware-based isolation
- Application control
- Access Control on Objects
- Exploit protection
- Malware protection
- Network protection
And here are some basic examples of ASR rules that Windows itself integrates.
- Block executable content from email client and webmail
- Block all Office applications from creating child processes
- Block Office applications from creating executable content
- Block Office applications from injecting code into other processes
- Block JavaScript or VBScript from launching downloaded executable content
- Block execution of potentially obfuscated scripts
- Block Win32 API calls from Office macro
- Use advanced protection against ransomware
- Block credential stealing from the Windows local security authority subsystem (lsass.exe)
- Block process creations originating from PSExec and WMI commands
- Block untrusted and unsigned processes that run from USB
- Block executable files from running unless they meet a prevalence, age, or trusted list criteria
- Block Office communication applications from creating child processes
- Block Adobe Reader from creating child processes
- Block persistence through WMI event subscription
However if we recall the definition of Attack Surface, stating that Attack Surface is the total of all possible paths an adversary can take in an attempt to breach, these are only the tip of iceberg surface reductions and there is a huge surface under the water! As previously mentioned http://techtalk.comodo.com/2020/08/27/comodo-mitre-kill-chain/ Kill-Chain Step 5 and onwards sorely lacks comprehensive ASR strategies.
OS/Kernel Attack Surfaces:
Now lets talk about my favorite layer, first let me tell you why it is my favorite layer
- Most powerful layer: this is where you OS Kernel lives and operates
- Most underutilized ASR applied layer
Imagine being able to use the power of this layer coupled with effectiveness of ASR techniques … extremely powerful combination.
This layer is responsible for running everything from a simple client computer, virtualized server or container workload running on the cloud, all of them are running on operating systems and interacting with OS Kernels for any type of communication or persistence in the systems. It truly is a magical layer for bringing heightened security.
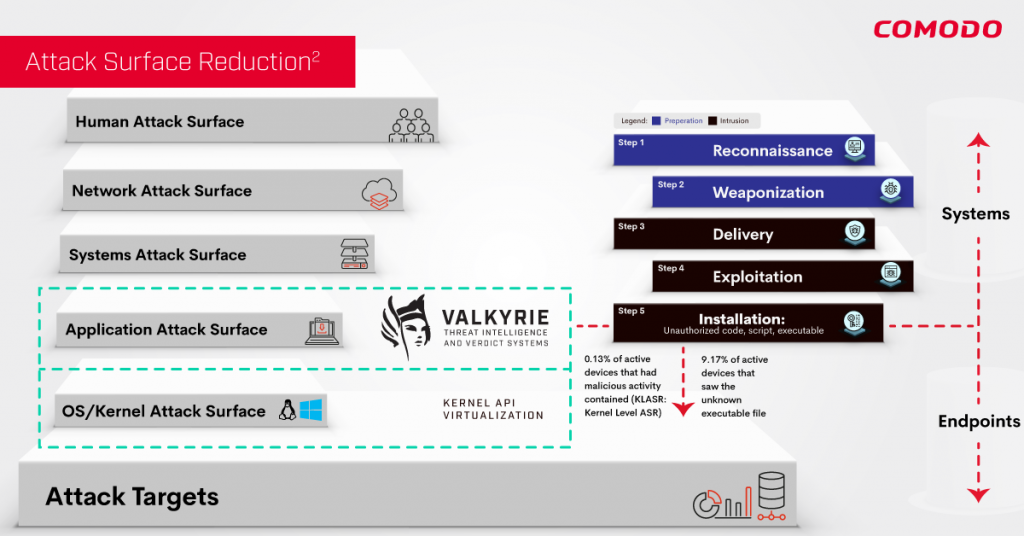
The real damage is done at Kill Chain-Step 5 and beyond. Because this is where the installation of malicious payload takes place. Rightly so the Cybersecurity world tries to stop them from reaching this layer, however we all know it’s a mathematical impossibility (The Halting Problem, Alan Turing). 100% detection is not Possible, adversaries will breach step-5, period! Therefore we propose that applying ASR on this powerful yet underutilized layer becomes of paramount importance!
Comodo introduces ASR2 : a holistic security architecture to minimize the attack surface on OS/Kernel layer. The reason why we name it ASR2 is because Comodo’s new architecture has two separate and very effective ASR techniques being applied to this powerful yet underutilized layer. Let me explain what these are:
- Executable/Code Level Attack Surface Reduction Technique (ELASR) :
With this technique, we only make full system resource available only to known good applications and processes. Whether these executables come in a .EXE or scripts running in an interpreted environment. They only get full access to system resource if they are known good. And we call her, Valkyrie !
Valkyrie is an infrastructure that has everything from AI to behavior analysis from static to dynamic analysis from algorithms giving verdicts to human brain giving verdicts. Lets take a look at actual historical data to see the power of ELASR. (Historical data set from 08/01/2020 to 08/31/2020 from enterprise customers).
- Device :
- 9.17% Percentage of active devices that saw an unknown executable file
- 90.83% Percentage of active devices that operated on known good state
- 0.13% percentage of active devices that had malicious activity running in Kernel API Virtualization contained (KLASR: Kernel Level ASR )
- 0% infection/breach
- File
- 97.31% Percentage of the unknowns that turn out to be clean
- 0.21% Percentage of the unknowns that turn out to be potentially unwanted application (PUA)
- 2.28% Percentage of the unknowns that turn out to be malware (to reemphasize none of these resulted in infection or breach as every unknown executable, which these files were, because they all were running in Kernel API Virtualization mode)
While in Auto Containment (Kernel API Virtualization), unknown files are simultaneously uploaded to Comodo Valkyrie, where every unknown file gets a trusted verdict, Good or Malicious:
Please note, Valkyrie is very different than other cloud based sandbox solutions, it doesn’t just rely on behavior analysis (dynamic analysis) to give a verdict,
Valkyrie analyze unknowns using two different verdicting methodology,
- Analyzing to find Good behavior
- Analyzing to find Bad behavior
Each submitted file undergoes further real-time analysis powered by Valkyrie global threat cloud, which is constantly collecting machine learning and AI derived IOCs from nearly 90 million sensors worldwide.
• Each file, to start with, is put through behavior analysis to identify malicious intent. Unknown executables are detonated in a virtual, cloud-based environment; all actions are monitored and analyzed. Processes spawned, files and registry key modifications, host state changes, and network activity are recorded. Such proactive behavior analysis can often accelerate the identification of zero-day malware.
• If a process is found to be malicious by Valkyrie, a Malicious verdict is assigned, and a unique identifier IOC signature is immediately returned to all networked endpoints.
• The file is quarantined or deleted from all managed endpoints (depending upon policy) and the local and global blacklists are updated.
• We don’t just rely on dynamic analysis as a final verdict If no malicious behavior identified by Valkyrie and submitted to our Global SOCs for in depth human analysis with an SLA of 4 hours. Please note: the reason Comodo is able assign human analysis is because of the innovation that reduces the attack surface to a limited few unknown.
• To preserve the integrity of the global whitelist, automated behavior analysis can add signatures only to the global blacklist. The status of ‘Good’ can only be granted to a file after in-depth checks by our cyber security analysts.
2-Kernel Level Attack Service Reduction: KLASR
Kernel API Virtualization is achieved by introducing virtualization layer between processes running unknown executable with Kernel functions. We have introduced 5 main virtualization components that virtualizes (Please Note: Virtualizing a Kernel API call and Hooking are two different methods) any relevant Kernel calls or callbacks. File System, Registry, Kernel Object, Service and DCOM/RPC are main virtualization components that both run in user and kernel mode.
Kernel API Virtualization, as described in my previous post http://techtalk.comodo.com/2020/08/17/comodos-patented-kernel-api-virtualization-under-the-hood/ provides protection against zero-day threats while having no impact on end-user experience. It provides security posture to protect without detection. It also provides a default-deny security posture with default allow security posture usability.
As can be seen, applying two ASR technique on the most powerful layer : OS/Kernel provides materially reduced attack surface which results in extremely heightened security posture.