Comodo XDR: eXtended Detection and Response : Discovering Unknowns, Revealing Hidden Threats

Comodo was one of the pioneers of Extended Detection and Response into network (XDR), web and cloud and I guess I am the one to blame as I charted and executed the strategy for this in 2017. A few months later, starting seeing other vendors announcing their NDR solutions, all of a sudden this concept quickly turned into XDR: eXtended Detection and Response. This quick evolution shows the need in the market place. Let me try to explain why EDR was not enough and never will be.
In 2018, ESG published a technical review of Comodo MDR service: https://www.esg-global.com/validation/esg-technical-review-comodo-mdr-security-operations-center-as-a-service
In that document, they stated that four most important attributes of a cybersecurity platform are:
- Broad coverage across threat vectors like email and web (38%)
- Central management across all products and services (33%),
- Capabilities across prevention, detection, and response (31%)
- and coverage that spans endpoints, networks, servers, and cloud-based workloads (27%)
On the tests carried out, we showed how we can trace and protect a breach over different types of assets and what additional visibility and threat hunting capabilities we provide fusing, aggregating and alerting over all those different kind of data sets and semantics.
But isn’t that what SIEM for I hear you asking?
Aggregating multiple telemetry sources, correlating different events, firing rules for automated detection. Not quite!
With traditional SIEMs you can EDR , Web Filtering, network traffic analysis, UEBA, IDS/IPS, etc. What you get is “layered visibility” over different security contexts. It is “not holistic” but also with very different resolutions as well. On EDR, you have Machine-Process-File relationship, on network traffic analysis: Source IP-Protocol Metadata- Destination IP, on UEBA User-Object-Action etc. Stitching them together is not possible without having the context as well as glue to fill-out the gaps between layers and dimensions. That is why traditional SIEMs, although they fill a void is no longer ideal in this world of complex threats and multiple attack surfaces. ESG research also shows that 66% of respondents who have tried post-processing EDR and NTA data found that effectiveness is limited because it is based on multiple independent point tools. So SIEM’s are inadequate solution where threat analysis required. So what is XDR then and how does it differ?
XDR: “eXtended Detection and Response” is a capability that arose from the needs of SOC teams and threat hunters. It not only delivers visibility into data across networks, cloud and endpoints, but also provides chaining of the missing pieces all together, adding the context and creating traceable events of actions between various different sources and dimensions of telemetry data. With XDR the security teams should be able to :
- Use it effectively for their daily threat hunting tasks using automated analysis, data pivoting, base-lining etc.
- Seeing the context of the data sources and relationship between different alerts
- Merge different context of information into common model, correlate them, track hidden threats
- Collaborate over cases and increase the productivity of the people operating the SOC
- Close investigations more quickly and efficiency.
So why a typical legacy EDR fails in helping threat hunters and SOC Analyst from revealing the unknowns threats?
Because EDR only has visibility to endpoint and NOT network and beyond. Basically getting the events only from Endpoints is no longer enough to have full situation awareness over any breach or incident. Our networks are made up of multiple asset types, not just one laptop, scattered across all interwoven in ways that a single endpoint has no visibility for. This is also reported in SANS report in 2018: EDR detects only 26% of initial vectors of attack, the rest is undetected and still unknown. Threat Hunters should offload all other sources of information into SIEM, build contextual information by themselves etc. In order to demonstrate this point lets take a legacy EDR provider like Crowdstrike and evaluate MITRE Attack Evaluation results for them : Lets analyse how Legacy EDRs like Crowdstrike do against undetected techniques during MITRE Attack Evaluation for APT 29: https://attackevals.mitre.org/APT29/results/crowdstrike/allresults.html
| Step | Procedure | Technique | Crowdstrike Detection |
| 1.A.3 | Established C2 channel (192.168.0.5) via rcs.3aka3.doc payload over TCP port 1234 | Uncommonly Used Port (T1065) |
No alerting on product side but MSSP report based on connection |
| 1.A.4 | Used RC4 stream cipher to encrypt C2 (192.168.0.5) traffic | Standard Cryptographic Protocol (T1032) |
No detection capability demonstrated for this procedure |
| 3.B.4 | Used HTTPS to transport C2 (192.168.0.5) traffic Evidence that the network data sent over the C2 channel | Standard Application Layer Protocol (T1071) |
No detection capability demonstrated for this procedure |
| 3.B.5 | Used HTTPS to encrypt C2 (192.168.0.5) traffic Evidence that the network data sent over the C2 channel is encrypted | Standard Cryptographic Protocol (T1032) |
No detection capability demonstrated for this procedure |
| 6.A.2 | Executed the CryptUnprotected Data API call to decrypt Chrome passwords | Credential Dumping (T1003) |
No detection capability demonstrated for this procedure |
| 6.B.1 | Exported a local certificate to a PFX file using PowerShell | Private Keys (T1145) |
No detection capability demonstrated for this procedure |
| 9.B.4 | Recursively collected files found in C:\Users\Pam\ using PowerShell | Data from Local System (T1005) |
No detection capability demonstrated for this procedure |
| 9.B.8 | Read and downloaded ZIP (working.zip on Desktop) over C2 channel (192.168.0.5 over TCP port 8443) | Exfiltration Over Command and Control Channel (T1041) |
No detection capability demonstrated for this procedure |
| 10.A.1 | Executed persistent service (javamtsup) on system startup | Service Execution (T1035) |
No detection capability demonstrated for this procedure |
| 10.B.2 | Executed PowerShell payload via the CreateProcessWithToken API | Execution through API (T1106) |
No detection capability demonstrated for this procedure |
| 11.A.14 | Used HTTPS to transport C2 (192.168.0.4) traffic | Standard Application Layer Protocol (T1071) |
No detection capability demonstrated for this procedure |
| 11.A.15 | Used HTTPS to encrypt C2 (192.168.0.4) traffic | Standard Cryptographic Protocol (T1032) |
No detection , a delayed An MSSP alert showed outbound connection with Cryptographic API calls to C2 server |
As it can clearly be seen legacy EDR products like Crowdstrike miss indicators of an attack if data is transmitted via network either via common ports or unknown ports. This means that they are totally blind over any C&C communication of an attack if a well-known blacklisted domain is not being used (catching already blacklisted domains is not the challenge, the unknown brand new threats that are operating out of sight is the problem). But aren’t C&C communication traces are important evidences and IoCs against blocking an active breach. Exactly !!! They are a key component! Here let me post Comodo MITRE Attack maps to show where regular EDR products are blind. Yes C&C Stage is exactly where “Active Breach” starts …
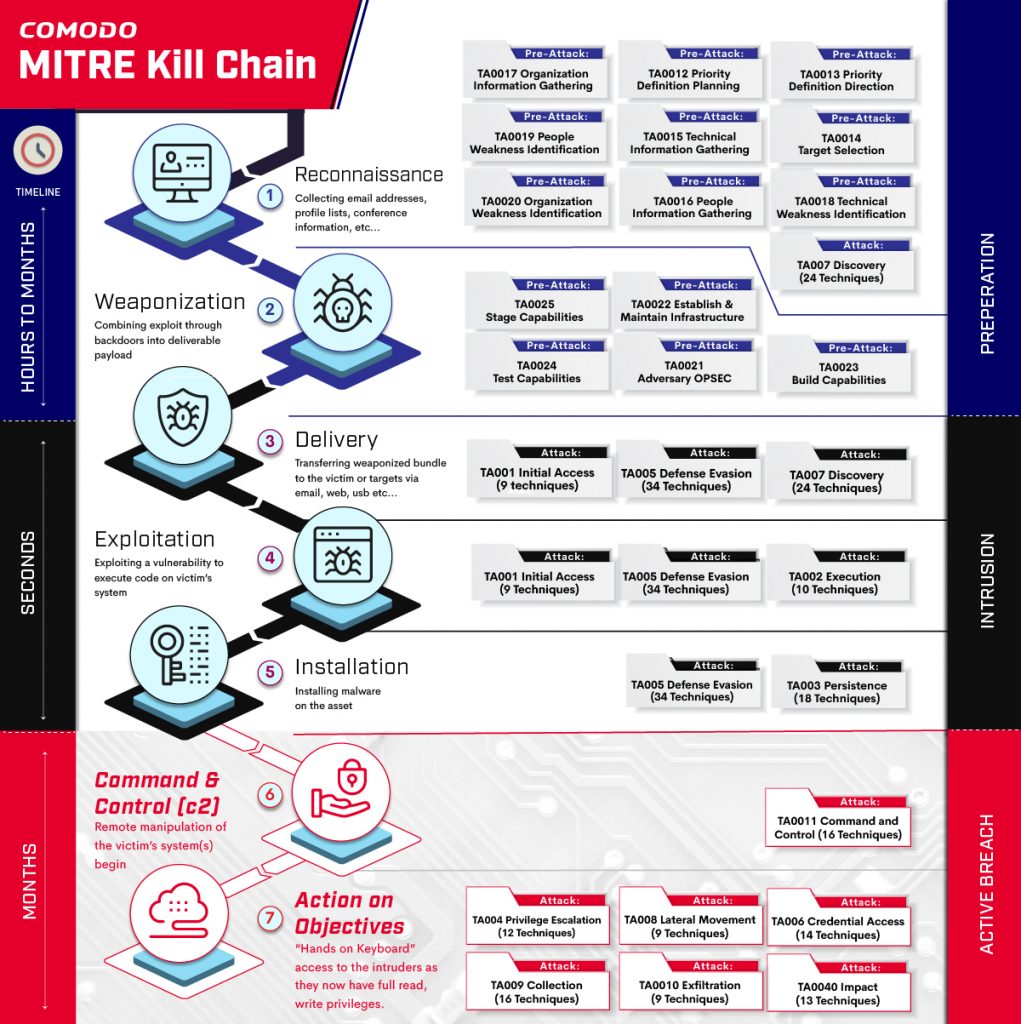
Comodo XDR has covered all stages of active breach, has endpoint agents to protect and analyze endpoints, network probe for network traffic analysis, cloud connectors to collect various events from multi-clouds, analytics and investigation platform to aggregate all the data and a security service layer to support 24/7 SOC and Threat Hunting services.
Comodo XDR endpoint agents discover all unknowns: files, scripts, assets etc. using its Containment (a combination of Kernel API virtualization, whitelisting, machine learning, behavior analysis, and advanced static and dynamic threat cloud analysis (Comodo Valkyrie)) to accurately and quickly deliver trusted verdict for unknown files and processes and turns all unknowns into known good or bad http://techtalk.comodo.com/2020/08/17/comodos-patented-kernel-api-virtualization-under-the-hood/, this reduces the attack surface and necessary investigation cycles drastically. Its endpoint sensors use “Adaptive Event Modeling”: where not only correlations but the sensor data itself can be extended in real time, enabling system to collect more information from the endpoints, do event chaining and enrichment on the endpoints and send all to the cloud if needed. The endpoints also provides semantics to the events detected by using first order logic, such as an adaptive discrete event modeling adding “Time-Series as a Dimension” and build a baseline model to detect anomalies (like insider threats where data must be collected and correlated from multiple inputs/assets over time).
Comodo XDR cloud collectors collects and analyze not on just computing resources of cloud providers but also gather all events from IaaS, PaaS, Serverless and SaaS services like 0365, Azure AD, Google Cloud or AWS Cloudtrail and detect and alert any threat targeting the cloud workloads. This allows analyst to discover, monitor, and secure cloud accounts, compute and storage instances, and the control plane. In today’s network topology where we are more than just one laptop, connected to different assets and cloud assets, being able to provide visibility to every asset type that the company is connected to as well as correlate that intelligence is what modern day SOC Analysts and Threat Hunters are searching for.
Comodo XDR has enterprise-class network traffic analysis that detect suspicious behaviors, prioritize investigations into the highest risk threats, and automate response, it capture all network traffic, generate extensive metadata for all important network protocols (more than 50 protocol parser including L7) , send this data to the cloud to enrich and correlate it with endpoint sensor data. Only sensing through the endpoints (what CrowdStrike does limiting its sensing just the endpoints vs full network) will not reveal hybrid attack surface. XDR brings the perspective security analysts need to understand your hybrid attack surface from the inside out. It enables finding rouge devices and reports back any attack vector based on those undetectable devices as well.
Comodo XDR has its own cloud native SIEM (built ground up with Cybersecurity in mind) and analytics platforms that has artificial intelligence capabilities with semi-supervised artificial intelligence engine that learns from the activities,events and operations. It is cloud native technology that enables big data analytics and data lake over security events and incidents. It also enables collecting, correlating, and analyzing unstructured events, generate new events from base events and uses chain of event correlations to detect, enrich raw events. So analysts can query and correlate different dimensions other than predefined structured queries. This will empower analysts to detect cyber threats at an earlier stage or execution of the attacks and remediate.
Comodo XDR comes with a full blown SOC services where threat hunting teams are used over the alerts the system generated to detect any malicious activity and provide incident response with the customer. It incorporates artificial intelligence capabilities with semi-supervised artificial intelligence engine that learns from the activities and operations of Comodo’s cybersecurity experts, accelerating the detection and response to new threats.