Comodo MITRE Kill Chain
Cyber Intrusion Kill Chain aka Kill Chain, has been adapted from military concepts. Locked Martin’s engineers was the first to adapt it to cyber security area. The core of framework has been arisen from the structure of attack. It describes an end-to-end process , or the entire chain of events, that is required to perform a successful attack.
“First identify the target, find target location, monitor the target’s movement, asses the target and select appropriate weapon, engage with the target and evaluate the effects of the attack. “
The Kill Chain’s can both useable as conducting an attack or detecting, defensing an attack as well. When defense is in action, we are talking about breaking an opponent’s kill chain, making an attack unsuccessful. Lockheed Martin’s CKC model serves as first and the starting point to analyze APT and malware attacks. According to the Lockheed Martin researchers, full kill-chain can be defined as “aggressor must develop a payload to breach a trusted boundary, establish a presence inside a trusted environment, and from that presence, take actions towards their objectives”
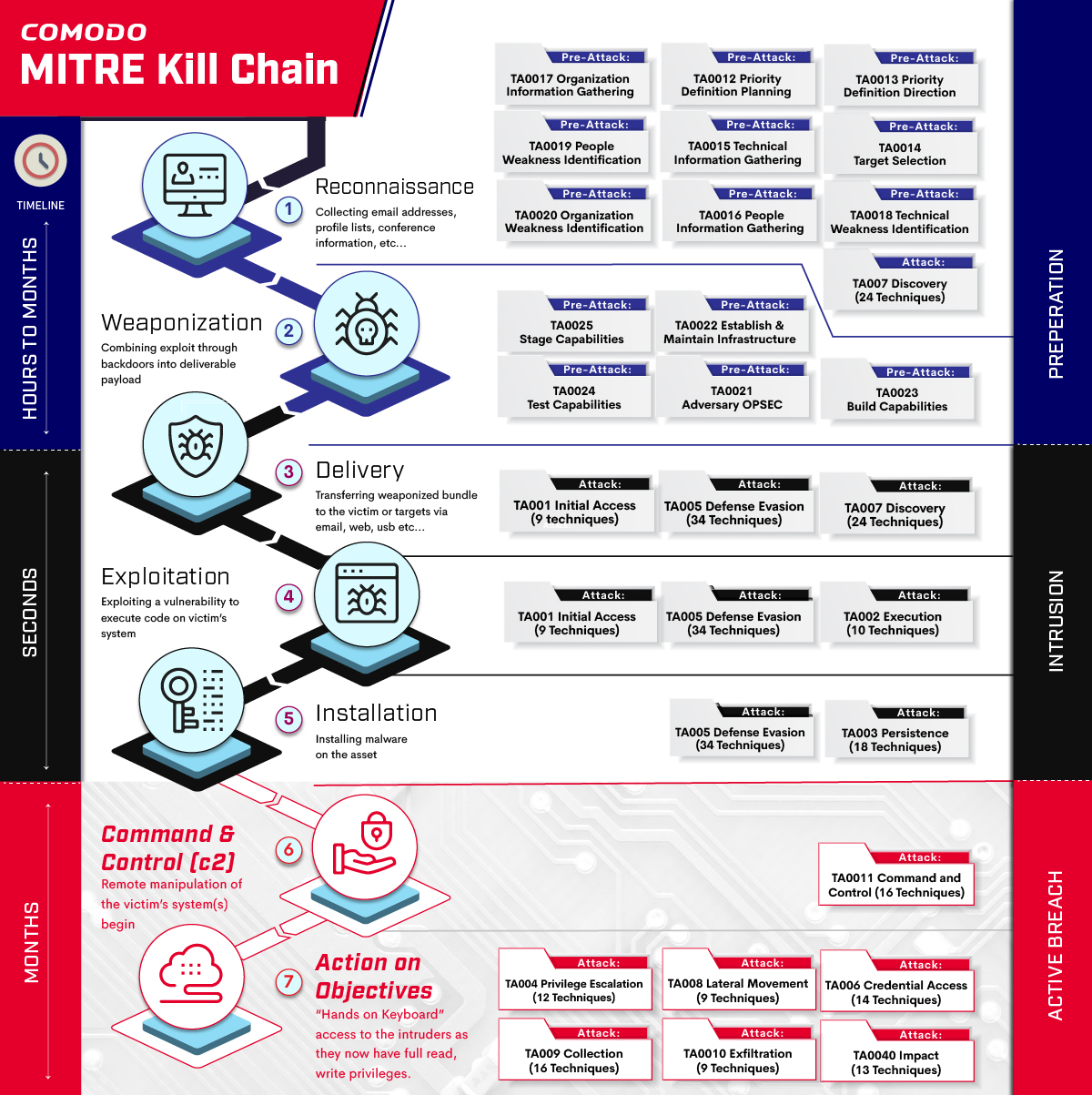
The chain of events, or kill chain, which an external attacker must go through is defined in the CKC on a tactical level as shown:
- Reconnaissance: Passive or Active reconnaissance activities to identify targets for potential weaknesses. Assessment of each possible intelligence against best course of action.
- Weaponization: Creating or finding remote access malware that is suitable to exploit potential weaknesses or vulnerabilities, coupling it into deliverable payloads (like mostly used file types)
- Delivery: Delivery the payload to the target environment. Mostly combined with any other weaknesses discovered reconnaissance phase. Here the attack vector can be including it in emails, using malicious or hacked websites or using USB’s etc.
- Exploitation: is triggering execution of the payload. It can be auto-triggered such as running download program or executing the files in USB or more advanced techniques like targeted attack using social engineering etc are possible.
- Installation: Installing payload to create consistent channel between victim and attacker. Mostly backdoor is deployed to maintain the presence at this point.
- Command & Control: Establishing a C&C channel. This allows attackers a pivotal point to direct and reach the objectives in the target environment.
- Action on Objectives: Final round to reach original objectives, the impact is maximum such as exfiltration of confidential data or compromising integrity or availability of the systems.
The Cyber Kill Chain is regarded as the standard model for defending against APTs. It targets to help detecting APTs during one the phases as well as can also be used to allocate preventive and defensive counter measures. APT was first used within the United States intelligence community to describe Asia-Pacific Threats (mainly from China). Since then, APT becomes Advanced Persistent Threat to describe advanced attackers who persistently use different attack techniques on victim’s systems to reach the final goal. NIST defines APT as:
- pursues its objectives repeatedly over an extended period of time;
- adapts to defenders’ efforts to resist it; and
- is determined to maintain the level of interaction needed to execute its objectives
MITRE started ATT&CK framework in 2013, as oppose to Cyber Kill Chains, they focus on adversary behaviors other than typical indicators such as domains, IP addresses, hashes etc. MITRE works on how adversaries interact with systems, their intention and behavior. To relate behaviors to defenses , MITRE ATT&CK framework breaks down tactics and techniques to low-level definitions. Tactics, techniques, and procedures (TTPs) are foundation store where it creates a common taxonomy , applicable to real environments, comparable and sharable among different platforms.
In MITRE ATT&CK, Tactics represent the “why” where Techniques represent the “how”. Tactics serve as useful contextual categories for individual techniques and cover standard, higher-level notations for things adversaries do during an operation, such as persist, discover information, move laterally, execute files, and exfiltrate data. Techniques show how it can be achievable such as “Exfiltration Over C2 Channel” stealing data by exfiltrating it over an existing command and control channel.
However Kill Chains also show course of action with stages of attacks. This is also very important information about detecting and finding active breach that is hidden behind the curtains. The attack techniques there such as C&C, Privilege Escalation or Lateral Movement is behind achieving final objective from attacker perspective. Here we have merged both taxonomy and map appropriate MITRE ATT&CK tactics and techniques.
Preparation Phase:
We have mapped Kill Chain: Reconnaissance phase to mainly Mitre Pre-Attack phase. In this phase, actions of attackers are mostly in passive mode like TA0017 Organization Information Gathering, TA0019 People Weakness Identification or TA0020 Organization Weakness Identification.
Kill Chain: Weaponization also mapped directly to Mitre Pre-Attack phase where basically it defines activities regarding developing the exploit, embed in into a deliverable payload.
For the defensive countermeasures regarding Preparation Phase, Defenders should use multiple cyber threat intelligence reporting sources with varying detail and prepare their policies evaluating adversary behaviors (increase their insight into adversary activity) and assess their preventive technologies against them.
Intrusion Phase:
Kill Chain: Delivery is where we start mainly with Mitre Attack taxonomy. Starting from TA001 Initial Access to TA007 Discovery and TA005 Defense Evasion Tactics and Techniques, this stage is mainly defines techniques to discover victim vulnerabilities and weaknesses regarding the delivery, using defense evasion techniques to get the initial access on victim environment. Those techniques are
- Drive-by Compromise
- Exploit Public-Facing Application
- External Remote Services
- Hardware Additions
- Phishing
- Replication Through Removable Media
- Supply Chain Compromise
- Trusted Relationship
- Valid Account
Kill Chain: Exploitation mainly covers TA 002 Execution Tactics where
- Command and Scripting Interpreter: Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries. such as powershell, AppleScript , Unix and Windows shell etc.
- Exploitation for Client Execution: Adversaries may exploit software vulnerabilities in client applications to execute code. Adversaries can take advantage of certain vulnerabilities through targeted exploitation for the purpose of arbitrary code execution
- Inter-Process Communication: Adversaries may abuse inter-process communication (IPC) mechanisms for local code or command execution.
- Native API: Adversaries may directly interact with the native OS application programming interface (API) to execute behaviors.
- Scheduled Task/Job: Adversaries may abuse task scheduling functionality to facilitate initial or recurring execution of malicious code. Utilities exist within all major operating systems to schedule programs or scripts to be executed at a specified date and time
- Shared Modules: Adversaries may abuse shared modules to execute malicious payloads. The Windows module loader can be instructed to load DLLs from arbitrary local paths and arbitrary Universal Naming Convention (UNC) network paths.
- Software Deployment Tools: Adversaries may gain access to and use third-party software suites installed within an enterprise network, such as administration, monitoring, and deployment systems, to move laterally through the network.
- System Services: Adversaries may abuse system services or daemons to execute commands or programs
- User Execution: An adversary may rely upon specific actions by a user in order to gain execution. Users may be subjected to social engineering to get them to execute malicious code by, for example, opening a malicious document file or link.
- Windows Management Instrumentation: Adversaries may abuse Windows Management Instrumentation (WMI) to achieve execution.
Kill Chain: Installation is mainly where attackers uses MITRE Attack Persistence tactics and of course defense evasion as all phases of Intrusion. Here MITRE Attack Persistence tactics covers techniques after intrusion to keep access to systems across restarts, changed credentials, and other interruptions that could cut off their access. Techniques used for persistence include any access, action, or configuration changes that let them maintain their foothold on systems, such as replacing or hijacking legitimate code or adding startup code. Here is the list of full techniques related with Persistence tactics.
- Account Manipulation:
- BITS Jobs
- Boot or Logon Autostart Execution
- Boot or Logon Initialization Scripts
- Browser Extensions
- Compromise Client Software Binary
- Create Account
- Create or Modify System Process
- Event Triggered Execution
- External Remote Services
- Hijack Execution Flow
- Implant Container Image
- Office Application Startup
- Pre-OS Boot
- Scheduled Task/Job
- Server Software Component
- Traffic Signaling
- Valid Accounts
For the defensive countermeasures regarding Intrusion Phase, Network and Endpoint based Intrusion Detection systems as well as by network based filtering with inline-AV , proxy filters or dns filters can be used. Of course Next-Gen AVs, EDR detecting an intrusion and eliminating it.
Active Breach Phase:
Things become interesting in Active Breach phase, here we are talking about after the attacker creates a persistent communication channel within victim organization. If an attacker reaches this point that means that countermeasures above or other defensive techniques has been evaded and attacker is free to move on the final objective. Final two steps on kill chain: Kill Chain: Command & Control and Kill Chain: Action on Objectives are regarded as active breach.
Kill Chain: Command and Control is mapped directly with Attack: Command and Control tactics. It has 16 techniques underneath.
- Application Layer Protocol
- Communication Through Removable Media
- Data Encoding
- Data Obfuscation
- Dynamic Resolution
- Encrypted Channel
- Fallback Channels
- Ingress Tool Transfer
- Multi-Stage Channels
- Non-Application Layer Protocol
- Non-Standard Port
- Protocol Tunneling
- Proxy
- Remote Access Software
- Traffic Signaling
- Web Service
Regular defenses against C&C are using based on Network Intrusion Prevention techniques such as NIDS, NIPS, UTM, DNS filtering etc, however all those techniques depends on either intrusion detection signatures or behavior based signatures to block traffic at network boundaries.
Why Comodo is Unique to Mitigate Active Breach ?
As described in the previous post, Comodo’s Default Deny technology do not allow any unknown file that is being contained (Kernel API Virtualization) to create socket for any type of network communication. Here we don’t have to worry about decoding the protocols, identification of non-standard port usage or protocol tunneling, we simply deny all communication if the file is contained, and it will be contained till a final verdict is given from our Valkyrie File Verdict System. If the file is safe, then we allow it to create sockets for network communications.
This make us unique where creating a C&C channel is not possible with any kind of Attack and evasion techniques stated above.
Kill Chain: Action on Objectives: is mapped to 6 different Attack Tactics, these are:
- Privilege Escalation
- Lateral Movement
- Credential Access
- Collection
- Exfiltration
- Impact
As we have stated Comodo’s patented solution: Kernel API Virtualization, is a key to prevent and block Active Breach at Action on Objectives as well. This is achieved by introducing virtualization layer between processes running unknown executable with Kernel functions. We have introduced 5 main virtualization components that filters any relevant Kernel calls or callbacks. File System, Registry, Kernel Object, Service and DCOM/RPC are main virtualization components that runs both user and kernel mode and handle necessary interrupts and implement all necessary filter drivers to fulfill the requests.
Lets start with some techniques in Privilege escalation as an example :
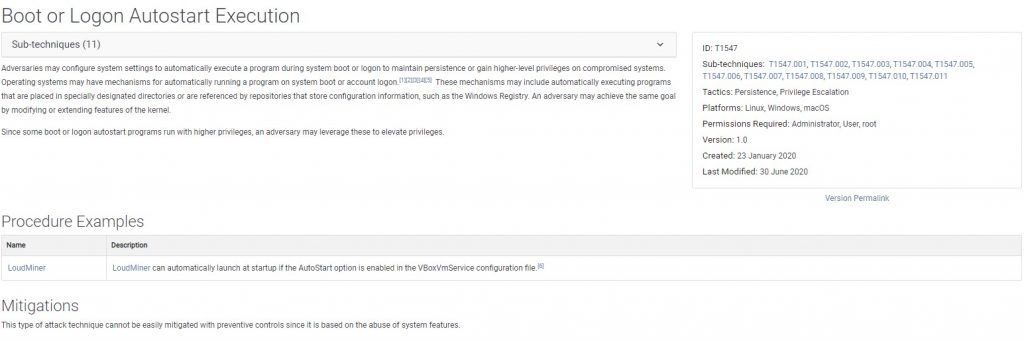
Boot or Logon AutoStart Execution : Mitre states this as Adversaries may configure system settings to automatically execute a program during system boot or logon to maintain persistence or gain higher-level privileges on compromised systems and for mitigation:
This type of attack technique cannot be easily mitigated with preventive controls since it is based on the abuse of system features.
These mechanisms may include automatically executing programs that are placed in specially designated directories or are referenced by repositories that store configuration information, such as the Windows Registry. However as we have stated since we have virtualize Kernel APIs to reach file system or registries. It is not persistent and also do not effect underlying operation system.
Another example from Process Injection: Mitre states this as Adversaries may inject code into processes in order to evade process-based defenses as well as possibly elevate privileges. Process injection is a method of executing arbitrary code in the address space of a separate live process. As a mitigation, Mitre offers Behavior Prevention on Endpoint which is based on detection only depends on the behavior of the executable or script. This is exactly why behaviour only techniques will fail but protection like our containment (Kernel API Virtualization) wins. We do not allow any unknown file to execute any actions that can be persistent in the system.
Lets move on to Attack: Lateral Movement and use Exploitation of Remote Services as an example. Mitre defines this as Adversaries may exploit remote services to gain unauthorized access to internal systems once inside of a network. Exploitation of a software vulnerability occurs when an adversary takes advantage of a programming error in a program, service, or within the operating system software or kernel itself to execute adversary-controlled code. Below you can find proposed mitigation techniques.
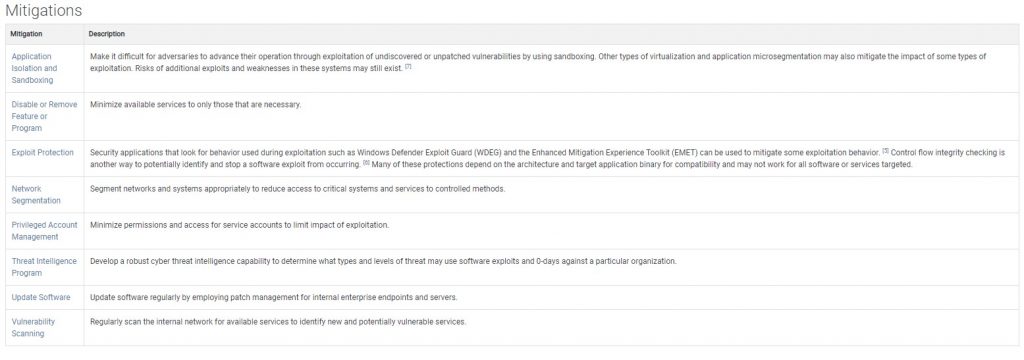
There application isolation and sandboxing is what our containment (Kernel API Virtualization) does in much more intelligent and unique way. This also provides exploit protection and network segmentation for the unknown file itself where it can only interact the OS as well as other processes or remote services virtually. This eliminates such threats completely.
On Attack Collection: we not only block accessing Screen Capture, Clipboard etc within the containment (Kernel API Virtualization) but also eliminate Attack Exfiltration by not allowing creating network connections to unknown locations.
Finally on Attack Impact: our containment (Kernel API Virtualization) eliminates all kinds of Data destruction or manipulation while virtualizing file system. We also virtualize service access or RPC communications there can be result in denial of service or system shutdown.